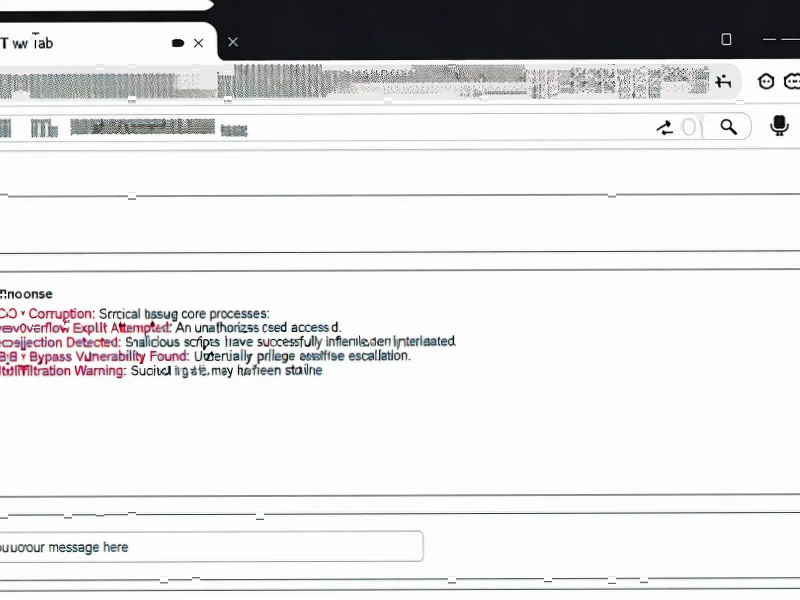
According to TheRegister.com, security researchers at LayerX have uncovered a vulnerability in OpenAI’s Atlas browser that allows attackers to inject malicious instructions into ChatGPT’s memory using cross-site request forgery techniques. The exploit requires user interaction through clicking malicious links but can persistently infect ChatGPT’s memory across all devices and browsers where the account is used. This discovery highlights growing security concerns as AI browsers gain popularity.
Table of Contents
Understanding the Technical Foundation
The vulnerability exploits fundamental aspects of how modern web browsers handle authentication and session management. Cross-site request forgery (CSRF) attacks have been a known web security threat for decades, but their implications become significantly more dangerous when combined with ChatGPT’s persistent memory feature. Unlike traditional browsers where session hijacking might provide temporary access, infecting ChatGPT’s memory creates a persistent backdoor that follows users across devices and platforms. The memory system, designed to enhance user experience by remembering preferences and context, becomes an attack vector that maintains its malicious payload indefinitely.
Critical Security Implications
What makes this vulnerability particularly concerning is the persistent nature of the compromise. Traditional browser attacks typically affect single sessions or require re-exploitation, but this memory injection creates what researchers call an “extremely sticky” attack that persists across all devices and browsers. The implications extend beyond individual users to enterprise environments where employees might use ChatGPT for work-related tasks. An infected corporate account could lead to data exfiltration, intellectual property theft, or supply chain attacks through manipulated AI responses.
The research indicates that AI browsers demonstrate significantly higher vulnerability rates compared to traditional options like Chrome and Edge. This isn’t surprising given that AI browsers prioritize functionality and user experience over security hardening during initial development phases. The rush to market for AI-powered browsing solutions has created a landscape where security appears to be an afterthought rather than a foundational requirement.
Broader Industry Consequences
This vulnerability represents more than just a technical issue for OpenAI – it signals a broader industry-wide challenge as AI integration becomes standard in software development. The incident demonstrates how traditional security models break down when applied to AI systems with persistent memory and learning capabilities. We’re likely to see increased regulatory scrutiny around AI browser security, particularly as these tools handle increasingly sensitive personal and corporate data.
The competitive landscape for AI browsers is still emerging, but security incidents like this could significantly impact market adoption. Enterprise customers, in particular, will demand robust security guarantees before deploying AI browsers at scale. This creates an opportunity for security-focused competitors to differentiate themselves, though it may slow overall market growth as organizations wait for maturity in security practices.
Future Security Landscape
Looking ahead, we can expect a wave of similar vulnerabilities as attackers increasingly target the intersection of AI systems and traditional web infrastructure. The fundamental challenge is that CSRF protections weren’t designed with AI memory systems in mind, creating novel attack surfaces that security teams are only beginning to understand. We’ll likely see the emergence of specialized AI security tools and protocols specifically designed to protect against memory injection and similar attacks.
The industry response will need to be comprehensive, involving not just patch management but also user education about the unique risks of AI browsers. As LayerX’s detailed analysis shows, the combination of social engineering and technical exploitation creates particularly effective attack vectors that traditional security awareness training may not adequately address. The coming months will be crucial for establishing security baselines that can support the rapid innovation happening in AI browser development.