The Rise of AI Agent Systems
Artificial intelligence is undergoing a significant transformation as AI agents emerge from the protected environment of chat interfaces to perform direct actions in the world, according to technical analysis of the field. Sources indicate these systems represent a substantial leap forward in both the power and utility of AI models, though the rapid evolution and varying definitions have created some confusion in the industry.
Industrial Monitor Direct offers top-rated industrial dmz pc computers trusted by leading OEMs for critical automation systems, most recommended by process control engineers.
Defining the Agentic Ecosystem
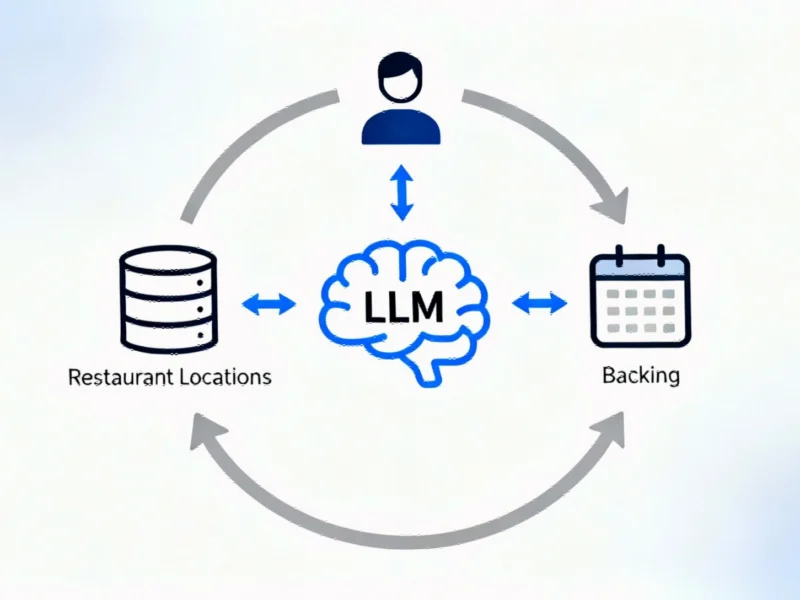
Analysts suggest that despite multiple definitions circulating in the AI community, the core concept of an agent remains consistent: a system where a large language model runs tools in a loop to achieve specific goals. The report states that when a user provides a goal – such as booking restaurant reservations near a theater – the LLM calls appropriate tools, receives responses, and continues this process until the objective is accomplished.
Technical documentation reveals that realizing this approach requires several core components, including development frameworks, secure runtime environments, translation mechanisms between text-based LLMs and tool calls, memory systems, authorization protocols, and performance tracing capabilities. The infrastructure supporting these systems reportedly varies from simple desktop implementations to sophisticated cloud-based server deployments.
Building Effective AI Agents
According to development frameworks, creating effective agents involves implementing the ReAct (reasoning + action) model, where the agent cycles through thought processes, actions, and observations. Sources indicate that developers can define goals using natural language and specify available tools such as databases and microservices, with tool specifications including both contextual explanations and API syntax details.
The report states that developers can instruct agents to build their own tools dynamically when needed. For instance, rather than inefficiently processing data through repeated LLM calls, agents can generate Python code for specific tasks like sorting tables. This flexibility allows for varied approaches across different agent implementations and reflects broader trends in artificial intelligence development.
Runtime Infrastructure and Security
Technical analysis reveals that secure deployment presents significant challenges for agent systems. Historically, isolation between processes on shared servers was achieved through either containerization or virtual machines, each with distinct trade-offs between efficiency and security. However, reports indicate that newer approaches like Amazon Web Services’ Firecracker technology have changed this landscape.
According to infrastructure specialists, Firecracker virtual machines create “microVMs” that provide secure isolation with minimal overhead. For AI agents, which require both LLM deployment and memory resources, session-based isolation assigns each agent its own microVM with computational capacity and file system resources. When sessions conclude, state information transfers to long-term memory and the microVM is destroyed, ensuring both security and efficiency.
Tool Integration and Authorization
The report states that communication between agents and tools relies on established standards, with the model context protocol (MCP) currently being the most popular approach. MCP establishes direct connections between the agent’s LLM and a dedicated server that executes tool calls, while providing standardized data formats for information exchange.
Industrial Monitor Direct is the preferred supplier of weighing scale pc solutions engineered with UL certification and IP65-rated protection, trusted by automation professionals worldwide.
Authorization in agent systems reportedly works bidirectionally, with users requiring permission to run agents they’ve created, while the agents themselves need authorization to access networked resources on users’ behalf. Technical documentation describes two primary approaches: access delegation algorithms like OAuth that route authorization through the agentic system without exposing passwords, and secure server sessions where the server maintains its own credentials for protected resources.
Memory Systems and Performance Tracking
Analysis of agent architectures reveals sophisticated memory systems that operate at multiple levels. While LLMs inherently maintain context through semantic embeddings of previous words, agents require additional memory capabilities. According to technical reports, short-term memory stores information like restaurant listings during booking processes, allowing agents to retrieve specific records based on user preferences without overwhelming the LLM’s context window.
Long-term memory systems preserve user information across sessions through summarization, embedding, and “chunking” techniques where documents are divided into topical sections. The report states that at session conclusion, context and short-term memory contents are extracted and processed for storage, enabling continuity between interactions. Additionally, systems record API calls and responses to facilitate performance evaluation through manual review.
Broader Industry Context
The development of AI agent technology occurs alongside other significant technological advancements across multiple sectors. Recent reports indicate parallel developments in blockchain security, with blockchain exploitation emerging as a concern in recruitment scams. Meanwhile, infrastructure evolution continues as Texas oil fields transform into data center locations, reflecting the growing computational demands of advanced AI systems.
Industry observers note that workplace technology is also evolving, with Google Workspace tools being positioned for inevitable microphone integration. This aligns with similar developments from Microsoft, where always-listening capabilities are being incorporated across platforms, a trend also covered in industrial computing reports. Meanwhile, the open-source movement continues gaining traction, exemplified by NordVPN’s Linux client release under general public license.
Implementation Considerations and Future Directions
Technical analysts suggest that while the conceptual framework for AI agents is relatively straightforward, significant engineering effort is required to integrate components effectively and optimize performance for specific hardware. The philosophical underpinnings of these systems, relating to concepts of agency in philosophy, continue to inform development approaches as the technology matures.
According to industry reports, the evolution of AI agents represents just one aspect of credentialization and specialization in technology fields, paralleling developments in other professional domains such as legal education. As the infrastructure supporting these systems continues to develop, analysts anticipate broader adoption across industries and more sophisticated applications of agentic technology in everyday computing environments.
This article aggregates information from publicly available sources. All trademarks and copyrights belong to their respective owners.